When receiving e-mail, you may be tracked to the sender's IP (if you send your computer's IP unintentionally when you receive the e-mail).
Fortunately, the Gmail system provides a way to prevent other parties from secretly tracking caller IP.
There is a technology that email service systems use as a way to determine whether a recipient has read the mail they send. After inserting an invisible image (pixel) in an e-mail message, when the mail contents are opened, the image is accessed and the recipient's IP address is tracked to obtain the location information.
Gmail can let you decide whether or not you want to selectively display the images included in your mail content, in a way that prevents you from inadvertently tracking IP addresses. If there is a suspicious image in the text, the image can be suppressed.
Therefore, if you do not want the sender of the email (including email system users other than Gmail users) to accept the mail receipt request, you can suppress the images included in the body text.
To disable automatic display of external images in Gmail, you can do this in Gmail -> Settings ->General-> Images.
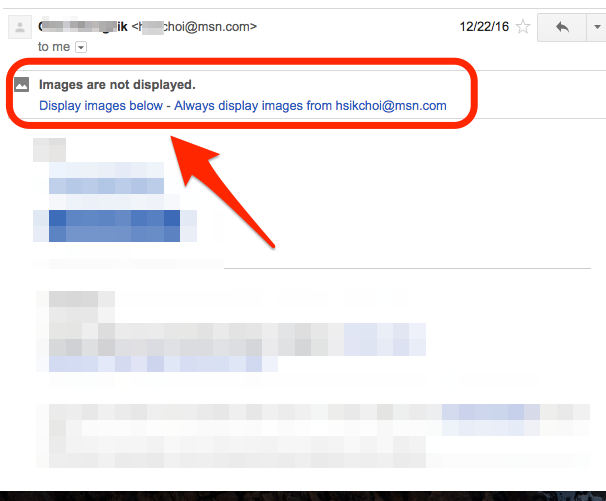
In this case, when the mail sender sends an e-mail asking to confirm receipt of the e-mail without knowing it, the following indication is displayed when receiving e-mail from Gmail.
If there is only text in the message body, but "Images are not displayed, it is likely that this message is the message that the other person has requested to acknowledge whether the message is opened or not. In this case, you do not have to display the image if you do not want to be notified of your receipt status.
In Gmail, the images contained in the message body provide a means of tracking outbound IP, or provide a number of security mechanisms to block information hacking using image insertion. For more information on this, please refer to the articles provided by Google.
-----------
Book:
New Advanced Chrome Device Management: Chrome Enterprise Kindle Edition
https://amzn.to/3SZIV96 Kindle Store - Paperback/Kindle Edition)